I’ve just installed Linux on PC and I’m already having fun with it.
So today I’ll be showing you how to use Nmap to scan and suck the information of the target
usingthe tools commands.
First of all you’ll need:
1) A Linux OS (Any Distro)(I’m using Mint Linux)
2) Nmap
If you don’t have Nmap installed don’t worry, Just open the terminal and type the command:
sudo apt-get install nmap
This will install Nmap. Now open a second tab and launch Nmap by typing “nmap”.
This will open a whole list of useful information read them line by line and understand the function of each command.
Now to the tutorial. First choose your target, it can be a Remote PC of your friend or a Web Server about which you want to get information about.
Now if you want to find out what type of OS your target is using then, Open a new Tab in the Terminal and type the following command:
nmap -v -A -O Target IP
Actually this command carries more then one function. It detects all the open Ports, The server OS, which is the “-O”
Now when you are done typing the command and the target, Press enter and let Nmap do it’s magic.
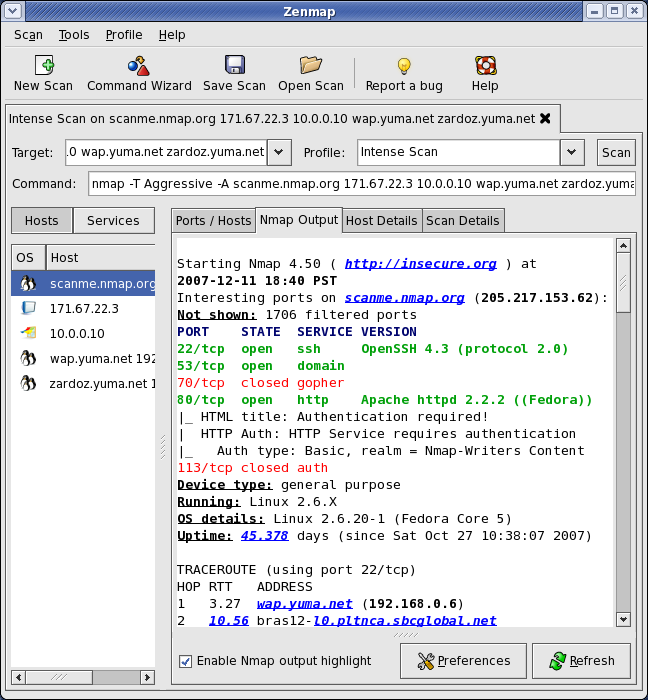
After the work is done you’ll get a similar output:



Don’t worry with the images. I’ve split them into three parts actually they are the result of the same scan.
Now as you can see in the pictures that Nmap has generated alot of useful information that might help a hacker exploit the site as well as help a security dude save his site by observing the open ports and restricting their access. You can see that Nmap has also given the OS of the server which in the above picture is “Linux”. It has also listed many open and vulnerable ports + SSH and SSL secure ports.
This ends my Nmap tutorial. Next time I’ll be posting a tutorial on hacking a remote PC with Nmap + Metasploit.













0 comments:
Post a Comment